Jonathan.Cohlmeyer.Dev|
unescaped-input.html
May 3rd, 2020
Unescaped Input & Code Execution
In December 2018 I got to thinking about how awesome it is that Statamic (a rad flat-file CMS) allows you to enter antlers (the Statamic templating language) directly in content fields... but wait ...
Does the CMS guard against users on the front end of the website entering antlers code into a contact form or login field?
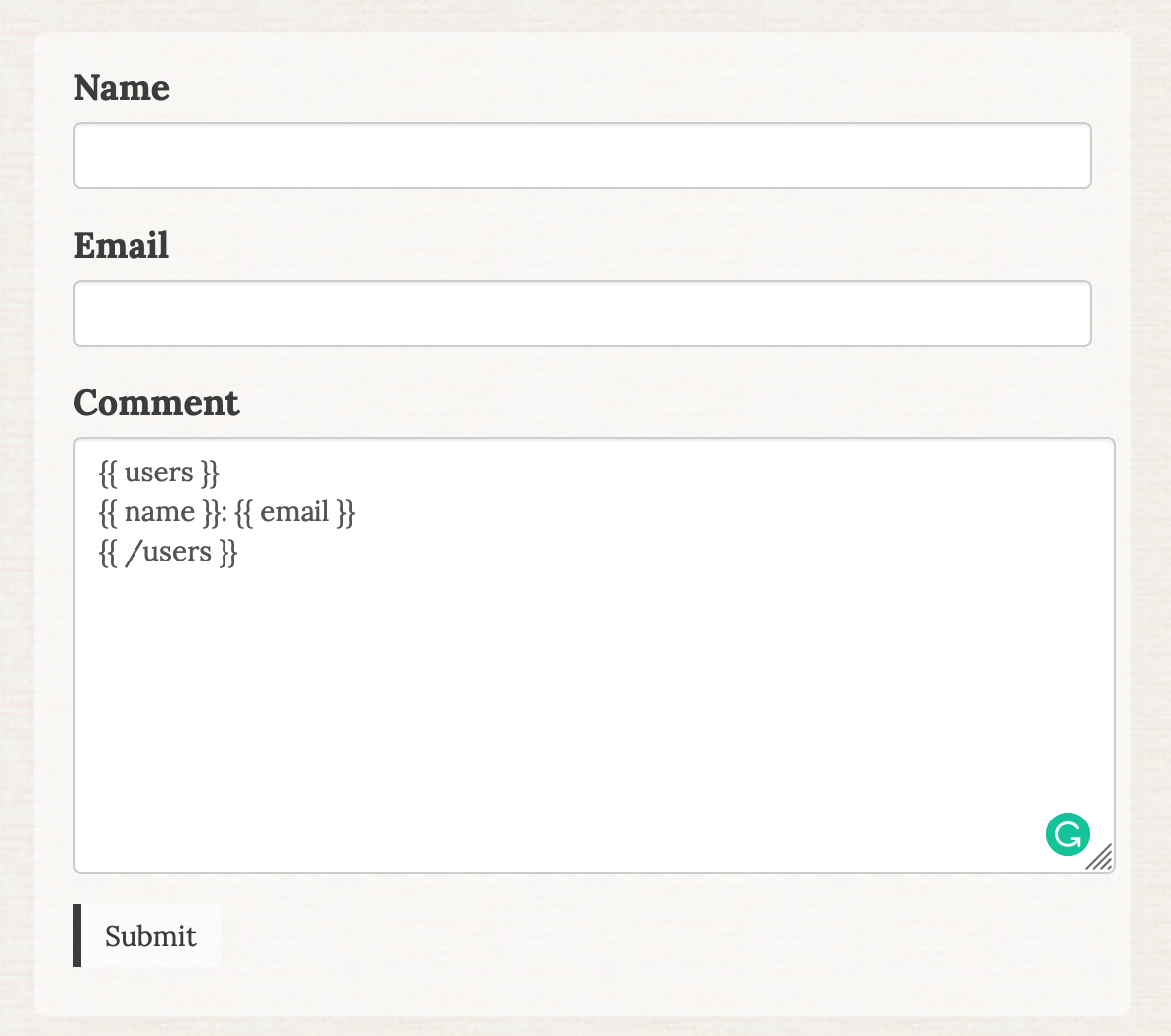
A statamic form with some antlers code typed into the content area.
I quickly went to my computer and fired up a contact form on a Statamic site I had built and was a little scared. I found that any antlers code that I put into a form field was executed when returning a form validation error. When the server placed the user-supplied value into the website using the {{ old:value }} tag in my template.
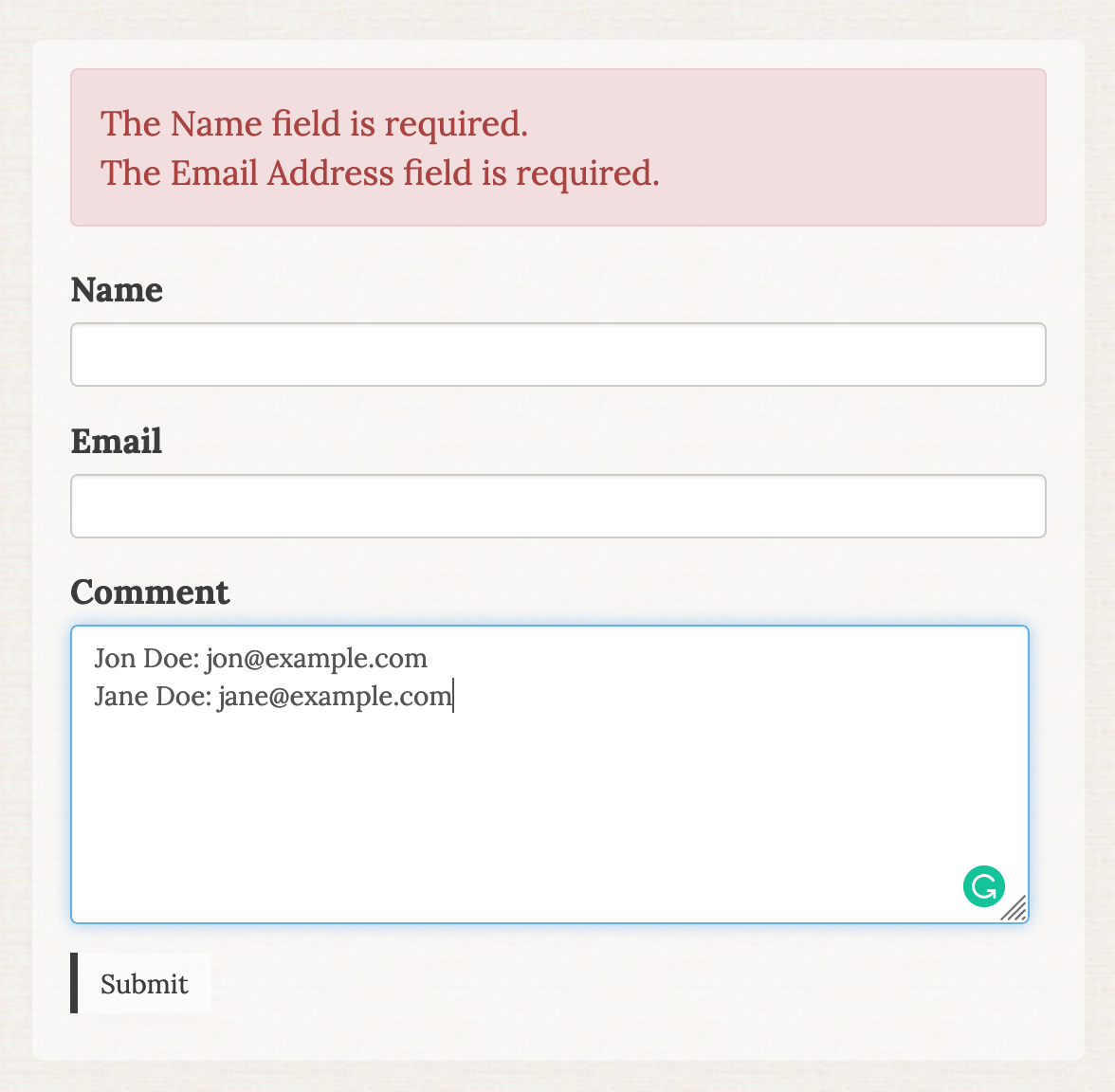
The filled out form returing an error and the results of the executed antlers code.
But wait, what does this mean?
In short, it means that anybody visiting my website could execute any antlers code on my website just by using my contact form, including getting secret keys stored in environment variables!
I messaged the Statamic core team and even though they were on Christmas vacation they took the report seriously and came out with a fix early in January with Statmaic version 2.7.3.
This fix makes sure that any input submitted through front end forms such as contact forms or workshop escape any curly braces used in the antlers templating language.
There is however one thing to note. Being able to execute antlers code in any content still means that someone who does have the limited permission to edit content in the CMS could write antlers code to gain access to data they may not be allowed to access, such as environment variables or other user's email addresses.
However, one could argue that if someone has access to log into the CMS you already have some level of trust with the user. Therefore you could argue the potential for abuse of code execution could be smaller.
However, I do wish there was at least an option to disable the execution of antlers code in content for users really concerned with security. Or alternatively, a way to limit who can write antlers code in content based on permissions. That being said the second option could get messy with multiple editors with different permissions.
All that being said, mixing code and content can be very powerful. However, this great power can cause security issues.
